Secure Integration of Third Party Services into ACGT Platform
 Introduction - Legal and Security requirements
Introduction - Legal and Security requirements
One of the most important constraints for the management of personal clinical and genomic data is the compliance to the ethical and legal data protection requirements. In ACGT a generic data protection framework has been defined which is based on a technical security infrastructure as well as on organizational measures and contractual obligations. Most of the technical requirements are dealt with the Grid infrastructure layer (GSI), which supports user authentication through digital signatures and also the delegation of user privileges to a service so that it can retrieve data or perform an action on the user’s behalf and without the user’s intervention.
Apart from the security requirements, the need in ACGT for a standard workflow definition language lead to BPEL, from the business process management world, as the most prominent and well supported technology. Nevertheless, the choice of BPEL gave rise to more requirements and challenges. The first one is the provision of a user friendly workflow authoring environment. The second relates to the need for an infrastructure that would make possible the invocation of the ACGT secure grid services from inside the BPEL-based workflows, since BPEL and the Web Services standard security specifications do not deal with such requirements. Another major challenge comes from the wish to integrate into BPEL workflows non-ACGT services, which is by itself a complex technological task in many aspects, let alone the challenges due to the legal and security requirements.
Proxy Services for credential delegation
The design methodology that was chosen to overcome the incompatibilities between the BPEL processes and the GSI secured ACGT services was to introduce a “layer of indirection”: the Proxy Services. The proxies, or wrapper services, provide BPEL friendly “facades” of the original, real ACGT services, effectively working as call transformation bridges between the two worlds (Figure). The core idea behind wrapper services is that we transform the interface of the underlying service and we pass extra pieces of information, which empowers us to detour the usual flow of credential delegation and bypass the Enactor but also at the same time to maintain all the required information so that we keep track of the “chain of responsibility”. All credential delegations are performed automatically inside a secure sandbox and are also logged in a database, thus we have also an effective mechanism for monitoring the whole process.
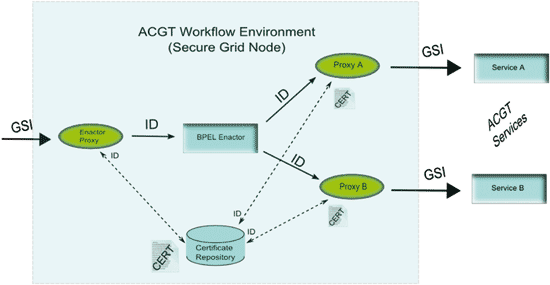
Proxy Services as interface adapters
The proxy service mechanism can also be used to provide higher level abstractions. An example of this is to remodel the interface of a service in order to simplify it and hide some technical details, thus aid in user friendliness of services. This wrapping technique has been applied to provide secure access to WSRF OGSA-DAI resources and simplify the connection to them by enclosing and hiding the technical hindrances of OGSA-DAI, like perform documents and stateful resources.
Another example is to provide access to many services through one proxy service which functions as a gateway, by dynamically creating custom interfaces. In the case of the “GridR Proxy Service”, by using this technique we were able to encapsulate the underlying “GridR Service” and hide its technical details, but also to support the notion of “Scripts as Services”, in which a different web service interface is exposed from the same single proxy service, depending on the actual R-script that is being “proxied”.
Proxy Services as gateways to 3rd party services
A major challenge in the ACGT workflow environment is to allow the integration not only of ACGT services. The integration into ACGT platform also of 3rd party services will greatly expand the abilities and the potentials of the platform and will provide to the end-users numerous helpful tools, far more than we could implement ourselves. The most prominent methodology to achieve this desirable augmentation is, again, through the proxy services mechanism.
First of all, it is a major challenge to integrate services which are heterogeneous, both syntactically and semantically, and enable them to interact while they use different protocols, data types and semantics. The use of proxy services can facilitate the required transformations and interpretations between the interacting parties and assist the mapping between different semantics or data types. One example where this technique has been applied with success is the integration of BioMoby services into ACGT workflows. The usage of a proxy service has been used in order to bridge the gap between the different semantics and transform the syntax of the messages exchanged between ACGT services and BioMoby services.
Furthermore, with the inclusion of 3rd party services into ACGT workflows, many legal and security aspects arise since we could potentially give access to sensitive data. By using proxy services, we ensure that this is done through a controlled sandbox and that we can enforce specific access policies. The proxy service can allow the access based on certain conditions and restrict the authorization to specific data resources, something which could otherwise be difficult to monitor.
Conclusion
The integration of 3rd party services into the ACGT platform is a complex technological task in many aspects, let alone also the need to comply with specific legal and security constraints. In order to accomplish this, the design methodology that has been chosen is the use of “proxy services”; mediator services that transform the interfaces, messages and the semantics of the interacting software components in order to bridge the gap between them. The major benefit drawn from the proxy services is the application of the security model that has been chosen for the ACGT platform and the enforcement of the legal requirements. This versatile approach has enabled us to integrate many heterogeneous tools into the ACGT platform and we still aim for the integration of many more. Note that some of the above-mentioned tools are still under development; nevertheless, prototypes are currently operating inside the ACGT platform.
Giorgios Zacharioudakis, FORTH
This article is based on the following publication:
S. Sfakianakis, L. Koumakis, G. Zacharioudakis, M. Tsiknakis, "Web-based Authoring and Secure Enactment of Bioinformatics Workflows", 4th International Workshop on Workflow Management (ICWM 2009), 4-8 May 2009, Geneva, Switzerland

